Guide to remove Magniber Ransomware and decrypt.magniber files in Windows 10, Windows 8, Windows 7, Windows Vista and Windows XP. Download Tool made by Trend Micro. Trend Micro Ransomware Decryptor is designed to decrypt files encrypted by 777 Ransom. For more information please see this how-to guide.
This holiday edition cover the latest ransomware news from the past two weeks, including known ransomware attacks and law enforcement takedowns.
Over the past two weeks, we have seen ransomware attacks on scent and flavor designed Symrise, FreePBX developer Sangoma, trucking giant Air Forward, and home appliance maker Whirlpool,
Of particular interest is the Air Forward attack as it was done by the new Hades ransomware operation that began operating last month and has been busy racking up victims.
This week’s other big news is the law enforcement takedown of the Safe-Inet and Insorg VPN and proxy services known for catering to cybercriminal activity.
According to Europol, threat actors using these services included ransomware operations, skimming attacks, and more.
“Active for over a decade, Safe-Inet was being used by some of the world’s biggest cybercriminals, such as the ransomware operators responsible for ransomware, E-skimming breaches and other forms of serious cybercrime,” Europol stated in a press release about the operation.
Contributors and those who provided new ransomware information and stories this week include @FourOctets, @PolarToffee, @DanielGallagher, @malwrhunterteam, @LawrenceAbrams, @struppigel, @fwosar, @VK_Intel, @jorntvdw, @serghei, @demonslay335, @malwareforme, @Ionut_Ilascu, @Seifreed, @BleepinComputer, @AhnLab_SecuInfo, @chum1ng0, @siri_urz, @Kangxiaopao, @Jirehlov, @fbgwls245, @M_Shahpasandi, and @S2Wlab.
December 19th 2020
New ANCrypted Ransomware
M. Shahpasandi found a new ransomware called ANCrypted.
December 20th 2020
Flavors designer Symrise halts production after Clop ransomware attack
Flavor and fragrance developer Symrise has suffered a Clop ransomware attack where the attackers allegedly stole 500 GB of unencrypted files and encrypted close to 1,000 devices.
December 21st 2020
Trucking giant Forward Air hit by new Hades ransomware gang
Trucking and freight logistics company Forward Air has suffered a ransomware attack by a new ransomware gang that has impacted the company’s business operations.
The Institute for Security and Technology (IST) Launches Multi-Sector Ransomware Task Force (RTF)
The Institute for Security and Technology (IST) — in partnership with a broad coalition of experts in industry, government, law enforcement, nonprofits, cybersecurity insurance, and international organizations — is today launching a new Ransomware Task Force (RTF) to tackle this increasingly prevalent and destructive type of cybercrime. The RTF’s founding members understand that ransomware is too large of a threat for any one entity to address, and have come together to provide clear recommendations for both public and private action that will significantly reduce the threat posed by this criminal enterprise.
BlackMamba Ransomware 2.0 discovered
S!ri discovered the BlackMamba 2.0 ransomware.
New cuteRansomware discovered
S!ri discovered a new ransomware called cuteRansomware.
December 22nd 2020
Magniber Ransomware Changed Vulnerability (CVE-2019-1367 -> CVE-2020-0968) and Attempted to Bypass Behavior Detection
Since September 23, 2019, CVE-2019-1367 vulnerability, which the developer of Magniber used for distribution, stopped operating in the systems with emergency security patch (Version 1903) applied. In response, the developer changed the latest vulnerability to CVE-2020-0968, expanding the infection target range. On top of this occurrence, CVE-2020-0968 security patch (distributed on April 15, 2020) cannot be applied to Windows 7 as it is no longer supported as of January 14, 2020. For better understanding of the changes, see figures below which are the comparisons between the codes before the change (including POC) and the those after the change.
Safe-Inet, Insorg VPN services shut down by law enforcement
Law enforcement agencies around the world in a coordinated effort took down and seized the infrastructure supporting Safe-Inet and Insorg VPN and proxy services known for catering to cybercriminal activity.
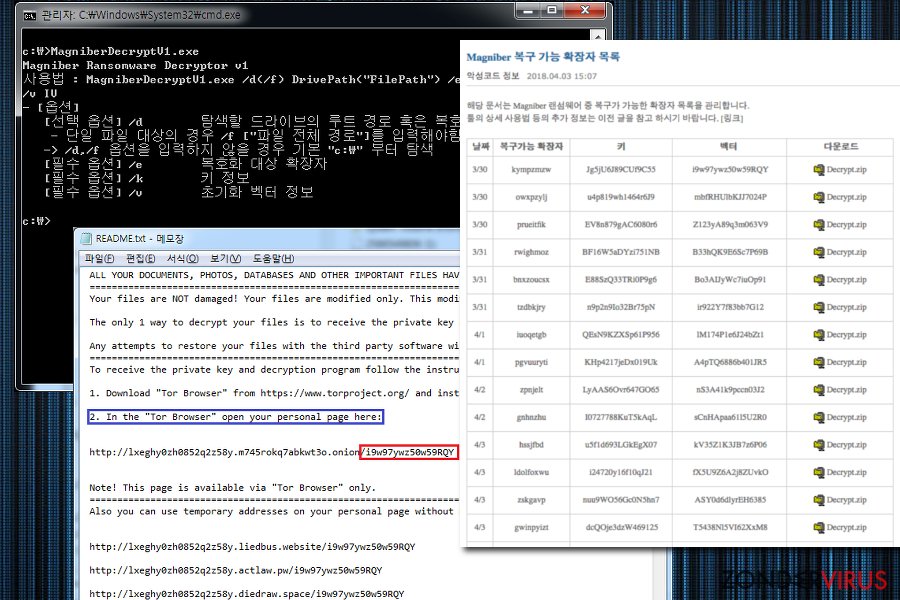
Ahnlab Magniber Decrypt V4
December 23rd 2020
New v316 ransomware
MalwareHunterTeam found a new v316 Jigsaw variant that pretends to be a ProtonVPN installer.
Story of the week: Ransomware on the Darkweb | W4 Dec
S2W LAB publishes weekly reports of the Ransomware activities that took place at Dark Web. Report includes summary of victimized firms, Top 5 targeted countries and industrial sectors, status of dark web forum posts by ransomware operator, etc.
December 24th 2020
FreePBX developer Sangoma hit with Conti ransomware attack
Sangoma disclosed a data breach after files were stolen during a recent Conti ransomware attack and published online.
New LOL Ransomware
xiaopao discovered the LOL ransomware that appends the .jcrypt extension to encrypted files.
New RansomeToad ransomware
xiaopao discovered a new ransomware called RansomeToad that appends the .rtcrypted extension.
New 21btc Dharma ransomware variant
xiaopao found a new Dharma ransomware variant that appends the .21btc extension to encrypted files.
New BlueEagle ransomware
xiaopao found a new ransomware called BlueEagle that appends the ..MaxSteel.Saher Blue Eagle extension.
December 25th 2020
New igal STOP Ransomware variant
Amigo-A found a new STOP ransomware variant that appends the .igal extension.
Unknown ransomware thinks it’s funny
MalwareHunterTeam found a new ransomware that appends the .HaHaHaHaHaHaHaHa extension to encrypted files.
Ahnlab Magniber Decrypt V4.1
New Mijnal Ransomware
Jirehlov Solace found a new ransomware that appends the .mijnal extension and drops a ransom note named OpenTheTorBrouser.html.
December 26th 2020
New PThree ransomware
Jirehlov Solace found a new ransomware named PThree that appends the .16x extension to encrypted files.
December 28th 2020
Home appliance giant Whirlpool hit in Nefilim ransomware attack
Home appliances giant Whirlpool suffered a ransomware attack by the Nefilim ransomware gang who stole data before encrypting devices.
New Lockedv1 ransomware
dnwls0719 found a new ransomware that appends the .lockedv1 extension and drops a ransom note named READMEV1.txt.
December 29th 2020
US Treasury warns of ransomware targeting COVID-19 vaccine research
The US Treasury Department’s Financial Crimes Enforcement Network (FinCEN) warned financial institutions of ransomware actively targeting vaccine research organizations.
That’s it for this week! Hope everyone has a nice weekend!
Source – Bleepingcomputer.com
Magniber
Magniber Ransomware is a cryptographic virus that has been spotted just recently. This threat has the typical malicious features of a Ransomware infection because it secretly applies an encryption to the victims’ files, adds a file extension and wants them to pay ransom in order to reverse the encryption. Shortly after its appearance, the malicious software has managed to launch several cyber-attacks and has affected various institutions, businesses, and regular online users. If you have been attacked, on this page, we will do our best to help you deal with Magniber Ransomware and minimize its harmful consequences.
Just read the information that follows and carefully proceed to the instructions in the removal guide below.
Magniber Ransomware – a new crypto virus that attacks different targets and wants a ransom
Magniber is a Ransomware threat that poses a serious challenge to security professionals. This malware has a unique encryption algorithm and creates a unique ransom message for the encrypted files. The hackers, who control the Ransomware, are using it to extort money out of their victims by depriving them of access to their own data. They place a ransom notification on the infected computer that informs the victim that they have to pay a certain amount of money for the recovery of the encrypted files. The payment is requested normally in Bitcoin, which is the preferred crypto currency used in many illegal operations. The pay-as-you-go system is legitimate, but the cyber criminals use it because it’s anonymous and untraceable. In the case of a Ransomware attack, it hides a great risk of losing your money without any chance of getting them back or trace them in case that the hackers disappear and do not send any decryption solution. For this reason it is advisable not to make any ransom payments but remove Magniber to protect your computer from further malware attacks.
If the guide doesn’t help, download the anti-virus program we recommended or try our free online virus scanner. Also, you can always ask us in the comments for help!
As for alternative methods of recovering your information, instead of paying ransom and not getting anything in return, there are some tools you can use. We have described several techniques for file-restoration under the article. However, before you take any action to recover them, first you should remove the Ransomware virus. To complete this task, we advise you to use the manual removal guide which can help you detect and delete the related malicious scripts. If you are not sure what exactly you have to delete, you may also help yourself with a security program such as the professional Magniber Ransomware removal tool that can remove spyware and malware from your computer. If your files are encrypted, we hope you have backups. This is the most efficient way to recover files, that’s why we advise our readers to back up their information always. But not all is lost if you don’t have any. Check your external drives, cloud storage, USB storage and other non-infected devices for copies or contact a professional for additional assistance.
Methods of distribution and infection of Ransomware
Ransomware viruses primarily attack victims with unprotected computers. Most often this malware spreads through spam, Trojan horses, and exploitation tools, but can be inserted into your computer system using an RDP attack as well. To protect your system, you have to do a few things and try not to repeat certain errors again. First, we advise you to secure your computer with an anti-malware program. Then back up your information. Copy your most important files and transfer them to an external storage such as a portable hard drive or USB memory. Keep it away from the computer and use it only when needed. And finally, we recommend updating your programs regularly. In other words, when your computer offers you to install an update to the programs you have, agree. You can also turn on automatic updates and save some time. Remember, you should never install software updates that come from non-reputed developers or sketchy pop-ups. Always stick to the official website and software developer and avoid installations from torrents, email attachments, pop-up links, and ads.
Remove Magniber Ransomware with security software or the manual removal guide
If you are one of those “lucky people” whose computer has been compromised by the Magniber Ransomware virus, you should remove the Ransomware as soon as possible. We advise you to try the easiest way and run a system scan using professional malware removal software. If you do not have any, there is the removal program available below. In case the malware prevents you from running security software, below you will find detailed instructions on how to detect and remove the malicious scripts manually.
Do not try to delete files you are not sure about and stick only to the removal guide. Any wrong attempts to uninstall the Ransomware on your own without knowing what you are doing can lead to failure or even more problems. In case of doubt, we suggest you leave us a comment or contact an experienced IT professional who have experience with viruses of the type.
SUMMARY:
| Name | Magniber |
| Type | Ransomware |
| Detection Tool | Some threats reinstall themselves if you don't delete their core files. We recommend downloading SpyHunter to remove harmful programs for you. This may save you hours and ensure you don't harm your system by deleting the wrong files. Download SpyHunter (Free Remover)*OFFER *Free Remover allows you, subject to a 48-hour waiting period, one remediation and removal for results found. SpyHunter's EULA, Privacy Policy, and more details about Free Remover. |
Magniber Ransomware Removal
You are dealing with a ransomware infection that can restore itself unless you remove its core files. We are sending you to another page with a removal guide that gets regularly updated. It covers in-depth instructions on how to:
1. Locate and scan malicious processes in your task manager.
2. Identify in your Control panel any programs installed with the malware, and how to remove them. Search Marquis is a high-profile hijacker that gets installed with a lot of malware.
3. How to decrypt and recover your encrypted files (if it is currently possible). You can find the removal guide here.
